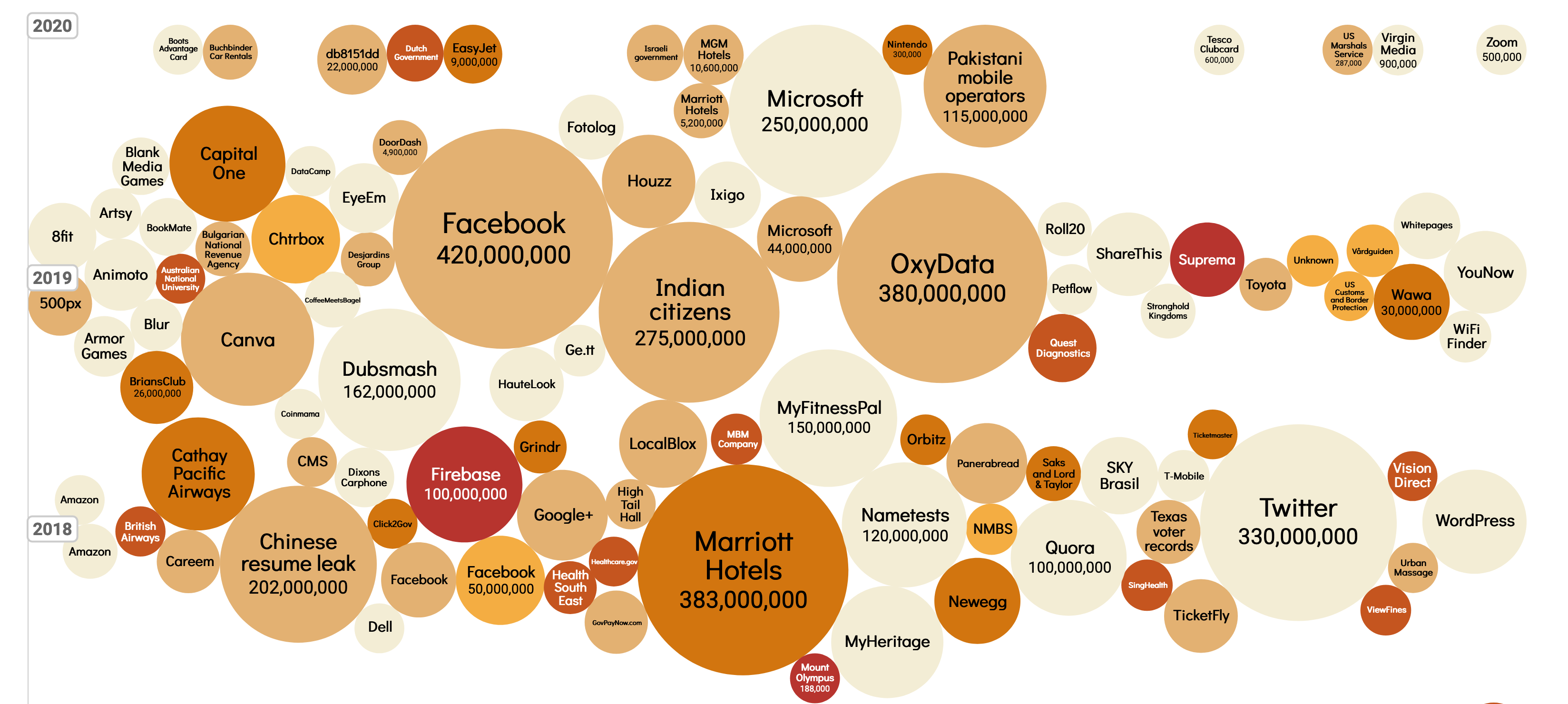
The State of Security
Security — both physical and digital — is at the forefront like never before. After the mega- breaches of 2018 and 2019, analysts were preparing for a year of unprecedented attention to security. That was before COVID hit.
Trends that had worried cybersecurity teams for years, like endpoint proliferation, reliance on cloud infrastructure and decentralized workplaces, have accelerated faster than anyone could have imagined.
Security Defined:
Security means protecting users’ data from misuse or disclosure to internal and external threats. It is foundational to privacy and reliability. Build an effective security infrastructure before you collect your first piece of customer data. Putting off security improvements is simply another way of accruing technical debt, and a dangerous one at that.
Key Trends in Security in 2020
SECURITY: TREND 1
The Rise of Multi-factor Authentication
In 2019, more than 4 billion records were exposed due to data breaches. Poorly secured identities and passwords are still our weakest link, especially in the face of social engineering and password-cracking tools. In fact, 81% of all confirmed data breaches involved weak, default or stolen passwords.
A key weapon for fighting back is to implement a multi-factor authentication (MFA) system that can help reduce the risk of identity compromise by more than 99.9%. By using biometrics and physical tokens such as the user's mobile device, organizations can increase safety and streamline the user experience, and industry partners can help scale while still ensuring personal privacy.
Georgian Impact Podcast
Episode 105: You Will Be Breached with Kerry Bailey
“You will be breached, you need to know where your data is, you need to know you're going to have vulnerabilities in this very distributed world."
Our Prediction
MFA Spreads to All Sectors and Company Sizes
Innovation and competition in the multi-factor authentication space will, for the first time, produce cost-effective and user-friendly solutions for SMBs to adopt in 2020, which will drive mass MFA rollout globally.
Best-in-Class Responses
WHAT TO DO
SECURITY: TREND 2
Extreme Proliferation of User Device Endpoints
The past decade has seen a significant switch from company-provided devices to bring-your-own-device (BYOD) policies. It’s no longer just smartphones, either — employees are now using their own laptops, tablets and smart watches at home and at work. In fact, Gartner, Inc. forecasts that the enterprise and automotive Internet of Things (IoT) market will grow to 5.8 billion endpoints in 2020, a 21% increase from 2019.
Our Prediction
Attackers Focus on IoT at Home
The more devices that are connected, the more vulnerable your network is to security threats, thus increasing your chances of malicious attacks from online sources and malware threats. We predict that a major vulnerability will be found in a consumer IoT device as attackers target the distributed workforce.
WHAT TO DO
SECURITY: TREND 3
Total Decentralization of the Workplace
WFH Security Policies Become Table Stakes
Many companies, for the first time, will need robust and scalable security infrastructure to manage sensitive business information on their employees’ home devices and networks. IT managers will need to assess the effectiveness of new solutions and roll out policies as quickly as possible to maintain the peak performance of their organizations.
Our Prediction
WFH Security Policies Become Table Stakes
Many companies, for the first time, will need robust and scalable security infrastructure to manage sensitive business information on their employees’ home devices and networks. IT managers will need to assess the effectiveness of new solutions and roll out policies as quickly as possible to maintain the peak performance of their organizations.
WHAT TO DO
Security: Key Takeaways
Now that you know what data you should be collecting, and your stakeholders are fully aware, it is your responsibility to protect it from bad actors.
Businesses have the opportunity to differentiate on security by protecting data from misuse or disclosure to internal and external threats and proactively planning for breaches. In summary, tech leaders should consider these important points in 2020:
Security Checklist
The Rise of Multi-factor Authentication
Extreme Proliferation of User Device Endpoints
Total Decentralization of the Workplace
Continue reading
This post is part of our 2020 State of Trust Report. If you don't see a menu on the left of your screen, dive into the rest of the report here.
